This article shows how to implement a Microsoft Account as an external provider in an IdentityServer4 project using ASP.NET Core Identity with a SQLite database.
Code https://github.com/damienbod/AspNetCoreID4External
Updated: You can also login using OpenID Connect instead of using Microsoft Account.
Updating Microsoft Account Logins in ASP.NET Core with OpenID Connect and Azure Active Directory
2019-05-17 Updated to OpenID Connect
2019-02-07 Updated to ASP.NET Core 2.2
2017-09-23 Updated to ASP.NET Core 2.0
Setting up the App Platform for the Microsoft Account
To setup the app, login using your Microsoft account and open the My Applications link
https://apps.dev.microsoft.com/?mkt=en-gb#/appList
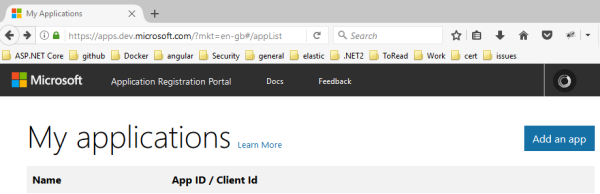
Click the ‘Add an app’ button
Give the application a name and add your email. This app is called ‘microsoft_id4_damienbod’
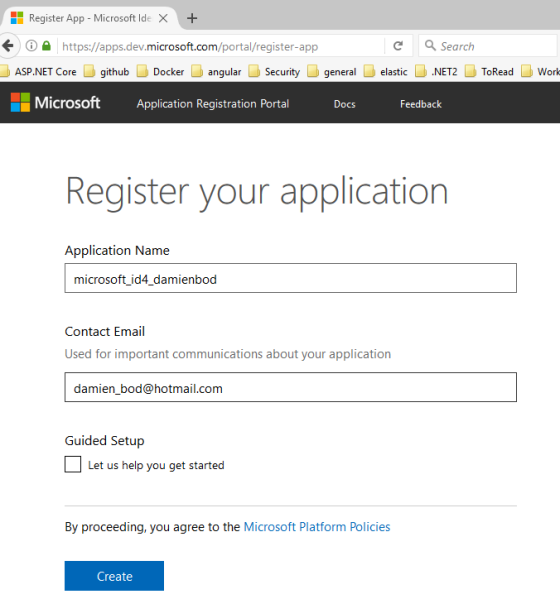
After you clicked the create button, you need to generate a new password. Save this somewhere for the application configuration. This will be the client secret when configuring the application.
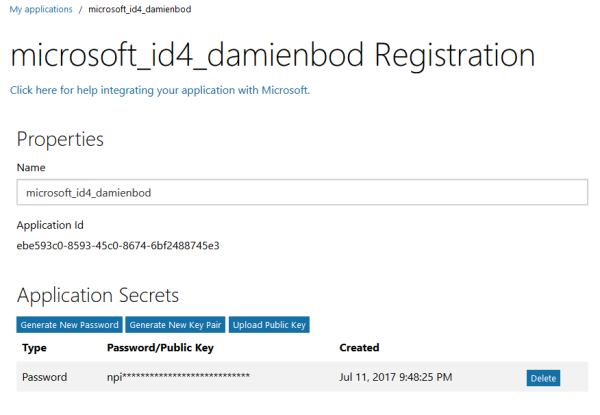
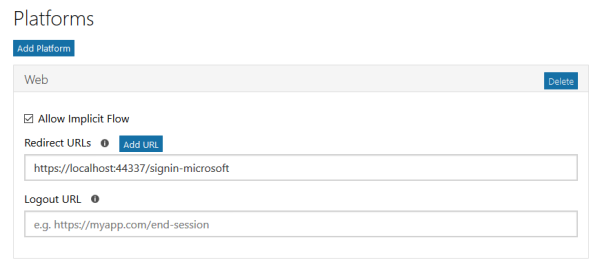
Now Add a new platform. Choose a Web type.
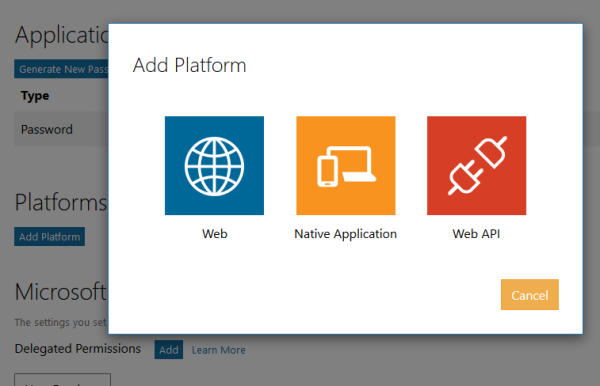
Now add the redirect URL for you application. This will be the https://YOUR_URL/signin-microsoft
Add the permissions as required
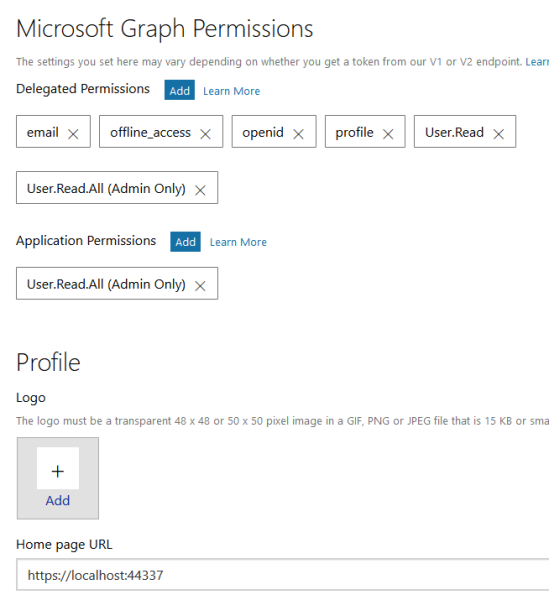
Application configuration
Note: The samples are at present not updated to ASP.NET Core 2.0
Clone the IdentityServer4 samples and use the 6_AspNetIdentity project from the quickstarts.
Add the Microsoft.AspNetCore.Authentication.MicrosoftAccount package using Nuget as well as the ASP.NET Core Identity and EFCore packages required to the IdentityServer4 server project.
The application uses SQLite with Identity. This is configured in the Startup class in the ConfigureServices method.
services.AddDbContext<ApplicationDbContext>(options =>
options.UseSqlite(Configuration.GetConnectionString("DefaultConnection")));
services.AddIdentity<ApplicationUser, IdentityRole>()
.AddEntityFrameworkStores<ApplicationDbContext>()
.AddDefaultTokenProviders()
.AddIdentityServer();
Now the AddMicrosoftAccount extension method can be use to add the Microsoft Account external provider middleware in the Configure method in the Startup class. The SignInScheme is set to “Identity.External” because the application is using ASP.NET Core Identity. The ClientId is the Id from the app ‘microsoft_id4_damienbod’ which was configured on the my applications website. The ClientSecret is the generated password.
services.AddAuthentication()
.AddMicrosoftAccount(options => {
options.ClientId = _clientId;
options.SignInScheme = "Identity.External";
options.ClientSecret = _clientSecret;
});
services.AddMvc();
...
services.AddIdentityServer()
.AddSigningCredential(cert)
.AddInMemoryIdentityResources(Config.GetIdentityResources())
.AddInMemoryApiResources(Config.GetApiResources())
.AddInMemoryClients(Config.GetClients())
.AddAspNetIdentity<ApplicationUser>()
.AddProfileService<IdentityWithAdditionalClaimsProfileService>();
And the Configure method also needs to be configured correctly.
app.UseStaticFiles();
app.UseIdentityServer();
app.UseAuthentication();
app.UseMvc(routes =>
{
routes.MapRoute(
name: "default",
template: "{controller=Home}/{action=Index}/{id?}");
});
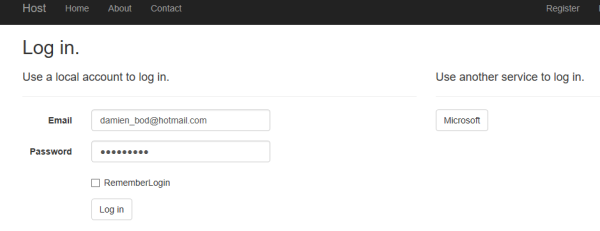
The application can now be tested. An Angular client using OpenID Connect sends a login request to the server. The ClientId and the ClientSecret are saved using user secrets, so that the password is not committed in the src code.
Click the Microsoft button to login.
This redirects the user to the Microsoft Account login for the microsoft_id4_damienbod application.
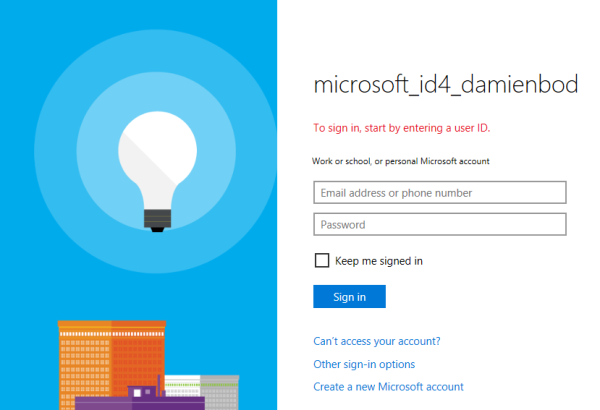
After a successful login, the user is redirected to the consent page.
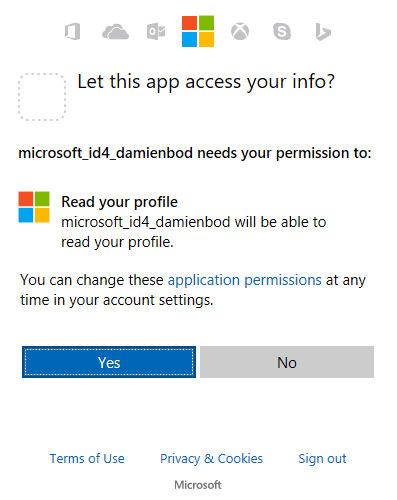
Click yes, and the user is redirected back to the IdentityServer4 application. If it’s a new user, a register page will be opened.
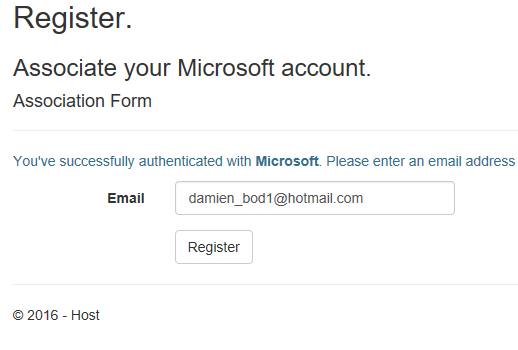
Click register and the ID4 consent page is opened.
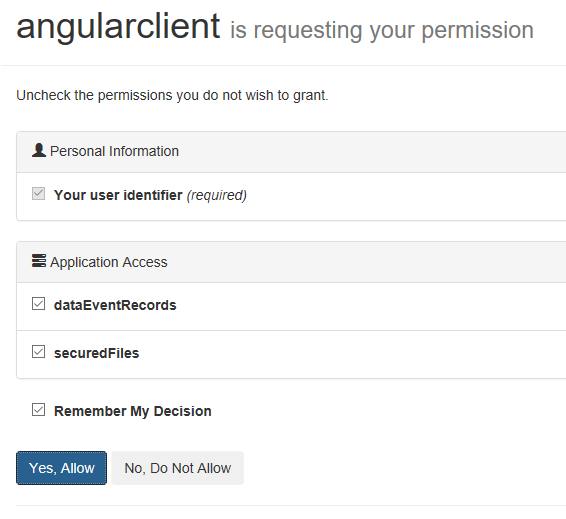
Then the application opens.
What’s nice about the IdentityServer4 application is that it’s a simple ASP.NET Core application with standard Views and Controllers. This makes it really easy to change the flow, for example, if a user is not allowed to register or whatever.
Links
Updating Microsoft Account Logins in ASP.NET Core with OpenID Connect and Azure Active Directory
http://docs.identityserver.io/en/release/topics/signin_external_providers.html

[…] Adding an external Microsoft login to IdentityServer4 (Damien Bowden) […]
[…] Adding an external Microsoft login to IdentityServer4 This article shows how to implement a Microsoft Account as an external provider in an IdentityServer4 project using ASP.NET Core Identity with a SQLite database. Give the application a name and add your email. […]
[…] should now be used instead of the AddMicrosoftAccount method. This replaces the existing post: Adding an external Microsoft login to IdentityServer4. It is still possible to use the https://apps.dev.microsoft.com if only Microsoft accounts are […]
Thanks, Domien. Wondering if you can help me with this SO question for Azure AD? https://stackoverflow.com/questions/59642367/auto-login-with-azure-ad-account-when-outlook-is-opened-idenity-server-4-for-au
I meant Damien* sorry.
Hi Neel not exactly sure how this should work, but I assume it should using an APP Registration in Azure with the same tenant as your office and the ID4 uses this for the login. Then the user is signed into the same Azure AD as you office.
Greetings Damien
How can I do the same but instead of taking the user to a MVC view incorporated in the identity server rather redirect him to a registration page inside a spa application? can you explain the workflow a bit?
[…] 7. Adding an external Microsoft login to IdentityServer4 … […]