Tag Archives: OpenId connect

Implement a secure Blazor Web application using OpenID Connect and security headers
This article shows how to implement a secure .NET 8 Blazor Web application using OpenID Connect and security headers with CSP nonces. The NetEscapades.AspNetCore.SecurityHeaders nuget package is used to implement the security headers and OpenIddict is used to implement the OIDC server. Code: https://github.com/damienbod/BlazorWebOidc OpenIddict is used as the identity provider and an OpenID connect […]

BFF secured ASP.NET Core application using downstream API and an OAuth client credentials JWT
This article shows how to implement a web application using backend for frontend security architecture for authentication and consumes data from a downstream API protected using a JWT access token which can only be accessed using an app-to-app access token. The access token is acquired using the OAuth2 client credentials flow and the API does […]
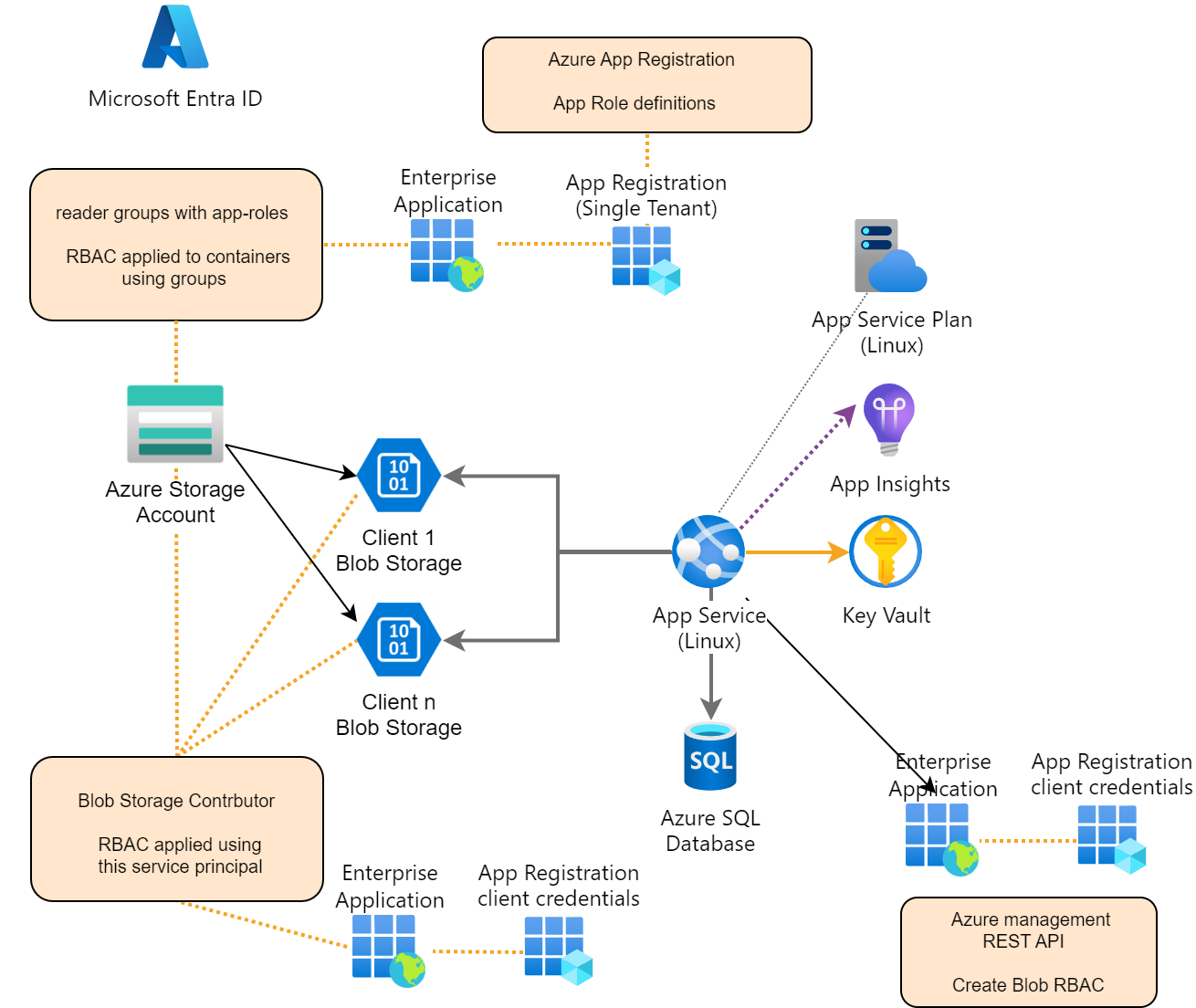
Multi client blob storage access using ASP.NET Core with Entra ID authentication and RBAC
This article shows how to onboard different clients or organizations in an ASP.NET Core application to use separated Azure blob containers with controlled access using security groups and RBAC applied roles. Each user in a client group can only access a single blob storage and has no access to blob containers belonging to different clients. […]
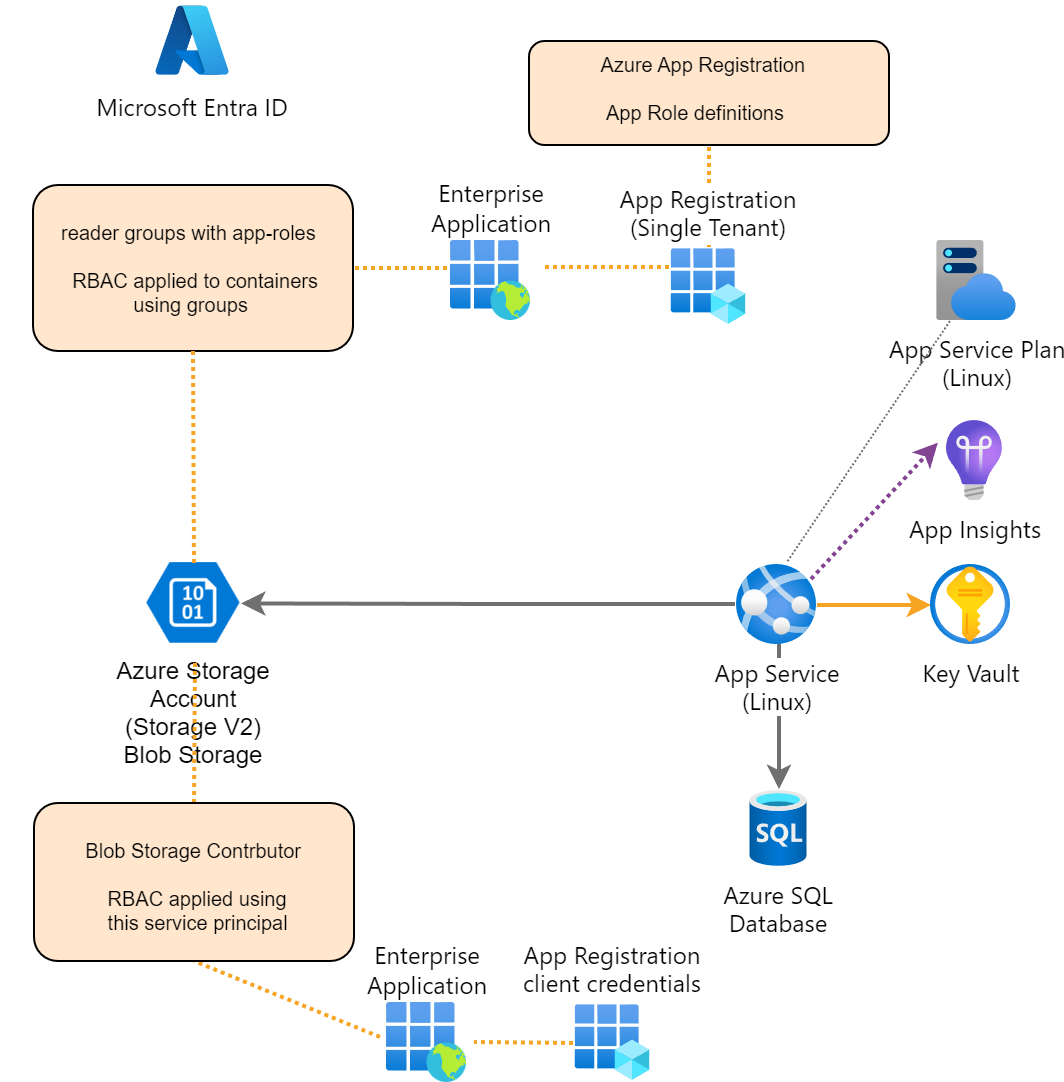
Delegated read and application write access to blob storage using ASP.NET Core with Entra ID authentication
This article shows how an ASP.NET Core application can control the write access to an Azure blob storage container using an application app registration. Microsoft Entra ID is used to control the user access and to implement the authentication of the web application. Code: https://github.com/damienbod/AspNetCoreEntraIdBlobStorage Blogs in this series The solution provides a secure upload […]

Secure an ASP.NET Core Blazor Web app using Microsoft Entra ID
This article shows how to implement an ASP.NET Core Blazor Web application using Microsoft Entra ID for authentication. Microsoft.Identity.Web is used to implement the Microsoft Entra ID OpenID Connect client. Code: https://github.com/damienbod/Hostedblazor8MeID Note: I based this implementation on the example provided by Tomás López Rodríguez and adapted it. Setup The Blazor Web application is an […]

Migrate ASP.NET Core Blazor Server to Blazor Web
This article shows how to migrate a Blazor server application to a Blazor Web application. The migration used the ASP.NET Core migration documentation, but this was not complete and a few extra steps were required. The starting point was a Blazor Server application secured using OpenID Connect for authentication. The target system is a Blazor […]
Securing a MudBlazor UI web application using security headers and Microsoft Entra ID
This article shows how a Blazor application can be implemented in a secure way using MudBlazor UI components and Microsoft Entra ID as an identity provider. The MudBlazor UI components adds some inline styles and requires a specific CSP setup due to this and the Blazor WASM script requirements. Code: https://github.com/damienbod/MicrosoftEntraIDMudBlazor Setup The application is […]

Authentication with multiple identity providers in ASP.NET Core
This article shows how to implement authentication in ASP.NET Core using multiple identity providers or secure token servers. When using multiple identity providers, the authentication flows need to be separated per scheme for the sign-in flow and the sign-out flow. The claims are different and would require mapping logic depending on the authorization logic of […]

Fix missing tokens when using downstream APIs and Microsoft Identity in ASP.NET Core
This article shows how a secure ASP.NET Core application can use Microsoft Entra ID downstream APIs and an in-memory cache. When using in-memory cache and after restarting an application, the tokens are missing for a value session stored in the cookie. The application needs to recover. Code: https://github.com/damienbod/bff-aspnetcore-angular OpenID Connect client setup The ASP.NET Core […]
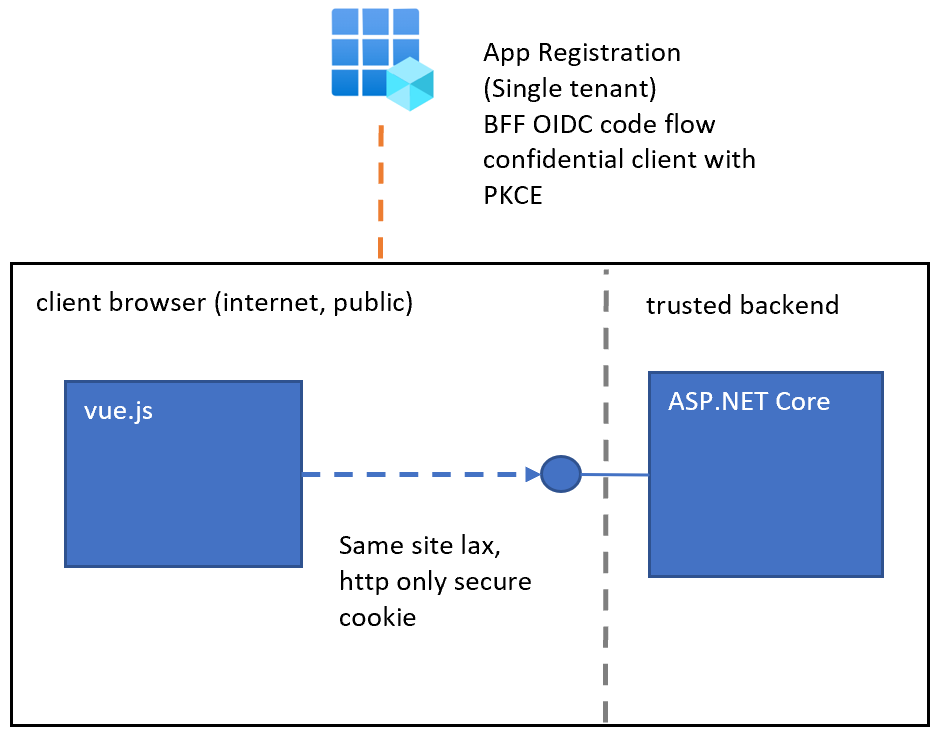
Implement a secure web application using Vue.js and an ASP.NET Core server
This article shows how to implement a secure web application using Vue.js and ASP.NET Core. The web application implements the backend for frontend security architecture (BFF) and deploys both technical stack distributions as one web application. HTTP only secure cookies are used to persist the session. Microsoft Entra ID is used as the identity provider […]
