Tag Archives: OIDC

Implement the On Behalf Of flow between an Azure AD protected API and an API protected using OpenIddict
This article shows how to implement the On Behalf Of flow between two APIs, one using Azure AD to authorize the HTTP requests and a second API protected using OpenIddict. The Azure AD protected API uses the On Behalf Of flow (OBO) to get a new OpenIddict delegated access token using the AAD delegated access […]

ASP.NET Core Api Auth with multiple Identity Providers
This article shows how an ASP.NET Core API can be secured using multiple access tokens from different identity providers. ASP.NET Core schemes and policies can be used to set this up. Code: https://github.com/damienbod/AspNetCoreApiAuthMultiIdentityProvider History 2023-04-29 Updated packages and revert to default JWT authorization packages due to errors on update. The ASP.NET Core API has a […]
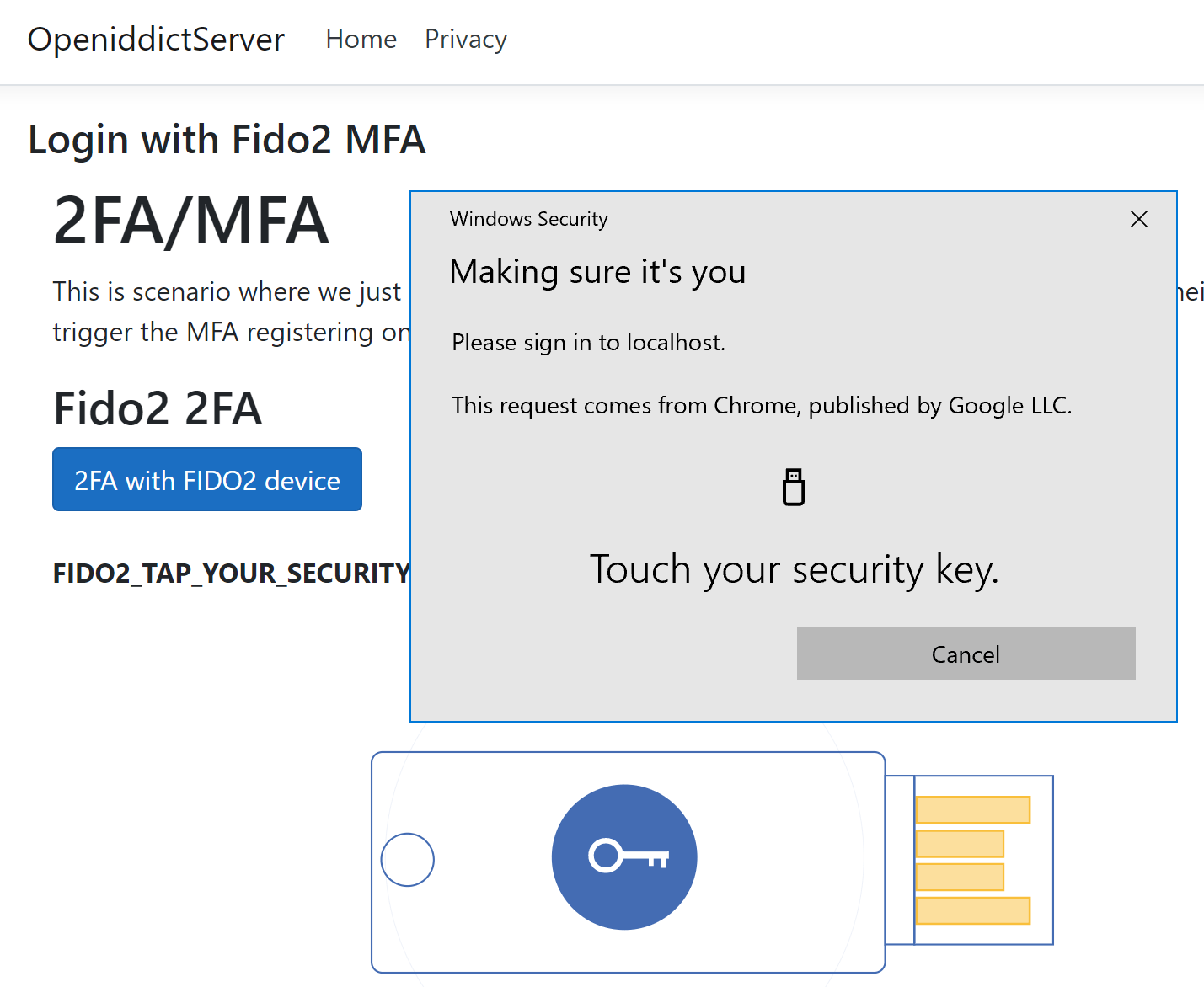
Add Fido2 MFA to an OpenIddict identity provider using ASP.NET Core Identity
This article shows how to add Fido2 multi-factor authentication to an OpenID Connect identity provider using OpenIddict and ASP.NET Core Identity. OpenIddict implements the OpenID Connect standards and ASP.NET Core Identity is used for the user accounting and persistence of the identities. Code: https://github.com/damienbod/AspNetCoreOpeniddict I began by creating an OpenIddict web application using ASP.NET Core […]

Implement Azure AD Continuous Access (CA) standalone with Blazor ASP.NET Core
This post shows how to force an Azure AD policy using Azure AD Continuous Access (CA) in an ASP.NET Core Blazor application. An authentication context is used to require MFA. The “acrs” claim in the id_token is used to validate whether or not an Azure AD CAE policy has been fulfilled. If the claim is […]
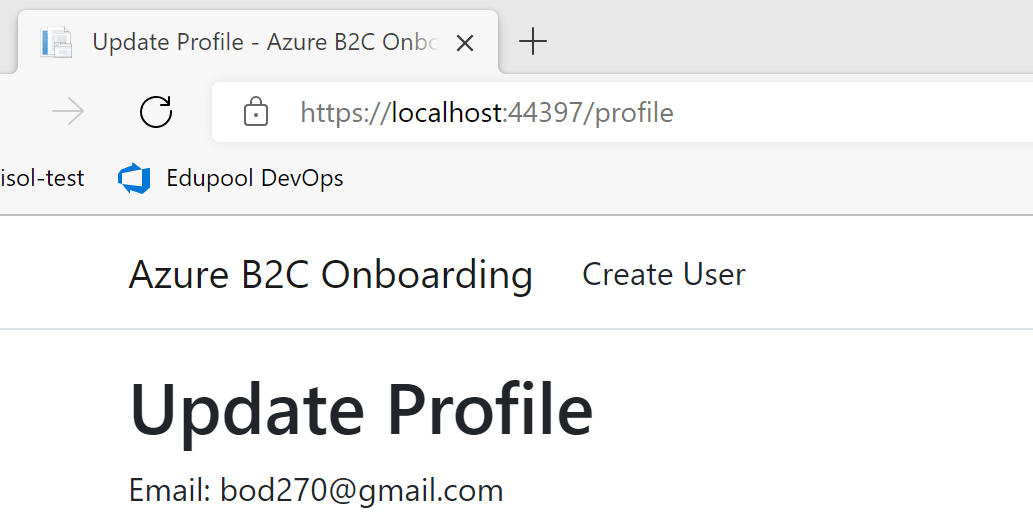
Onboarding new users in an ASP.NET Core application using Azure B2C
This article shows how to onboard new users into your ASP.NET Core application using Azure B2C as the identity provider and the account management. The software has application specific persisted user data and this user data needs to be connected to the identity data from the corresponding user in Azure B2C. Code: https://github.com/damienbod/azureb2c-fed-microsoft-entra-id History 2024-01-02 […]

Create Azure B2C users with Microsoft Graph and ASP.NET Core
This article shows how to create different types of Azure B2C users using Microsoft Graph and ASP.NET Core. The users are created using application permissions in an Azure App registration. Code: https://github.com/damienbod/azureb2c-fed-microsoft-entra-id History 2024-01-02 Updated to .NET 8, Graph SDK 5 The Microsoft.Identity.Web Nuget package is used to authenticate the administrator user that can create […]
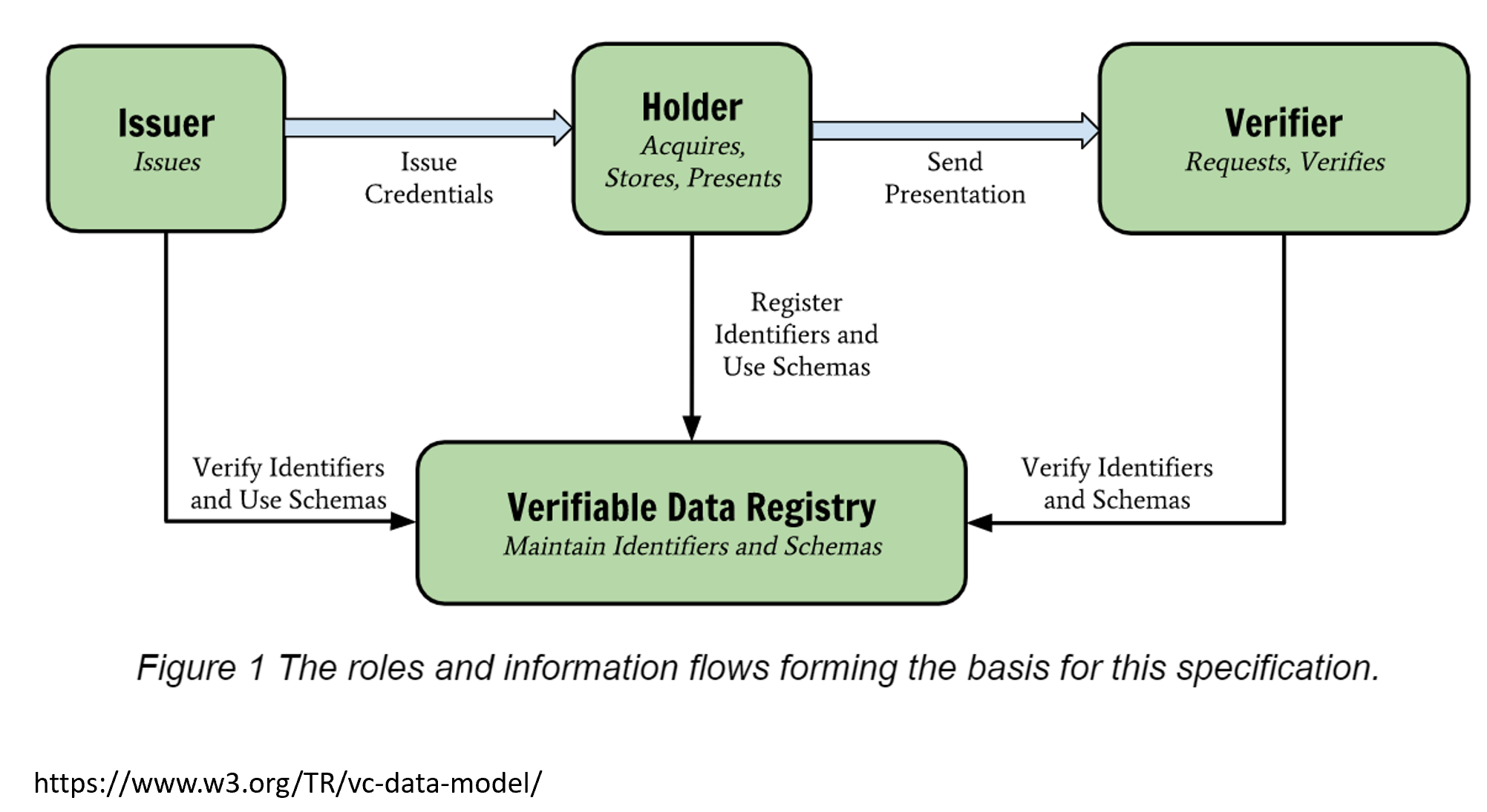
Problems with online user authentication when using self sovereign identity
Using self sovereign identity (SSI), there is no standardized solutions for solving online user authentication when using verifiable credentials and verifying the identity and user. All solutions result in further compromises and result in new problems. To understand the problems, we need to understand how this works. The following diagram shows the verifiable credential (VC) […]
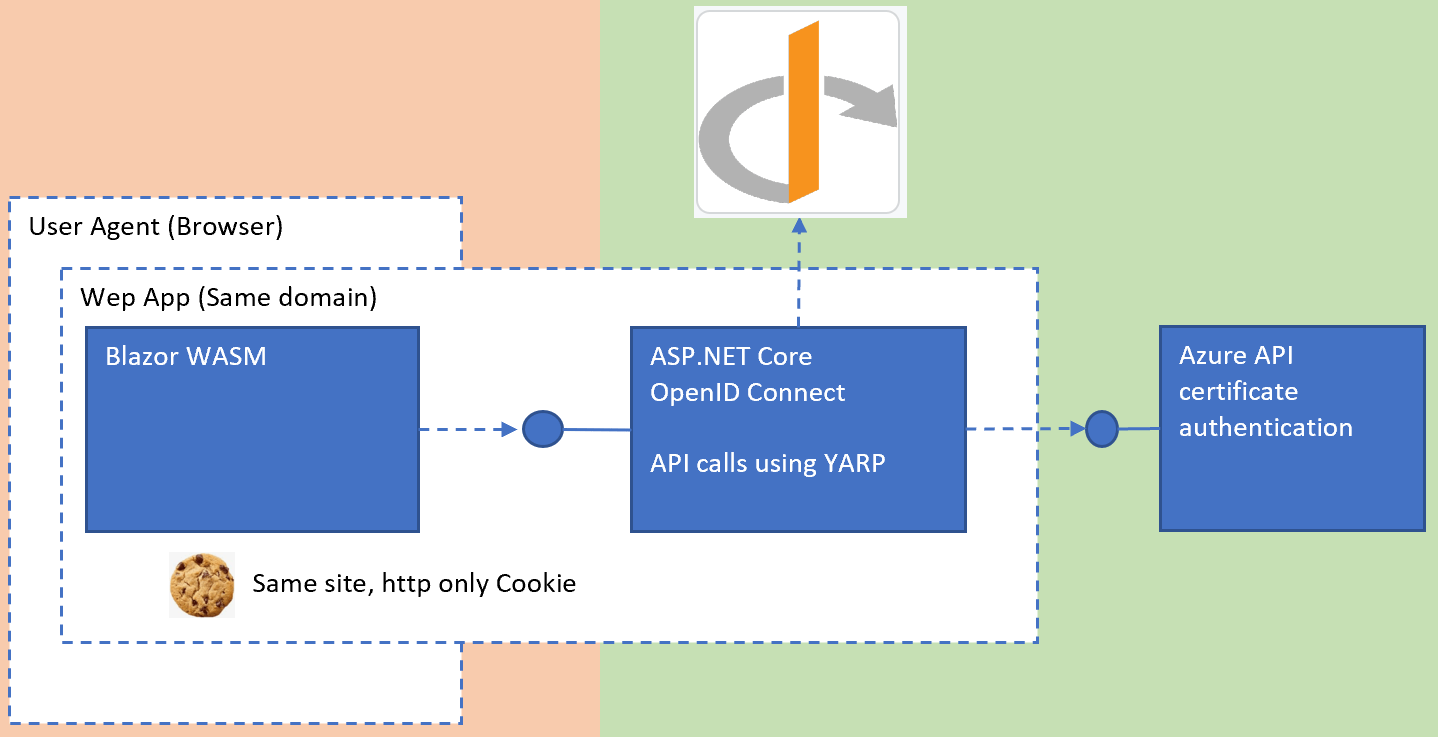
Using Blazor with a YARP downstream API protected using certificate authentication
This article shows how to use a downstream API protected with certificate authentication using Microsoft YARP reverse proxy from a Blazor application. The Blazor WASM HTTP requests are sent to a secured backend which uses YARP to forward the requests to the API protected with the certificate authentication. The Blazor application authenticates using the OpenIddict […]
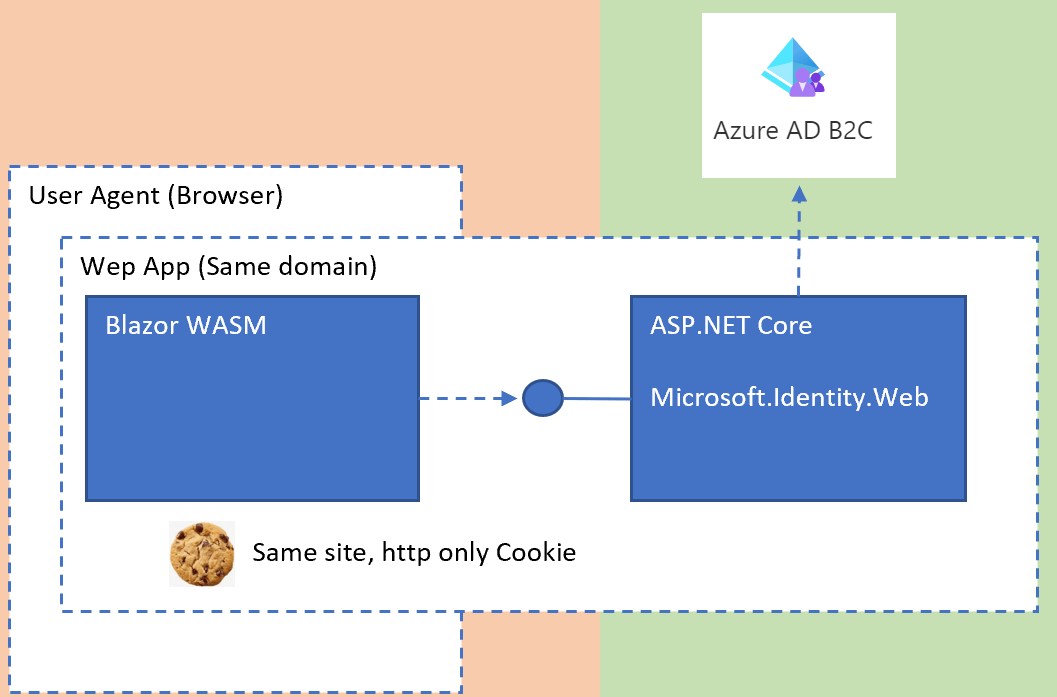
Implement a PWA using Blazor with BFF security and Azure B2C
The article shows how to implement a progressive web application (PWA) using Blazor which is secured using the backend for frontend architecture and Azure B2C as the identity provider. Code https://github.com/damienbod/PwaBlazorBffAzureB2C Setup and challenges with PWAs The application is setup to implement all security in the trusted backend and reduce the security risks of the […]

Comparing the backend for frontend (BFF) security architecture with an SPA UI using a public API
This article compares the security architecture of an application implemented using a public UI SPA with a trusted API backend and the same solution implemented using the backend for frontend (BFF) security architecture. The main difference is that the first solution is separated into two applications, implemented and deployed as two where as the second […]
