Tag Archives: AzureAD

Debug Logging Microsoft.Identity.Client and the MSAL OAuth client credentials flow
This post shows how to add debug logging to the Microsoft.Identity.Client MSAL client which is used to implement an OAuth2 client credentials flow using a client assertion. The client uses the MSAL nuget package. PII logging was activated and the HttpClient was replaced to log all HTTP requests and responses from the MSAL package. Code: […]
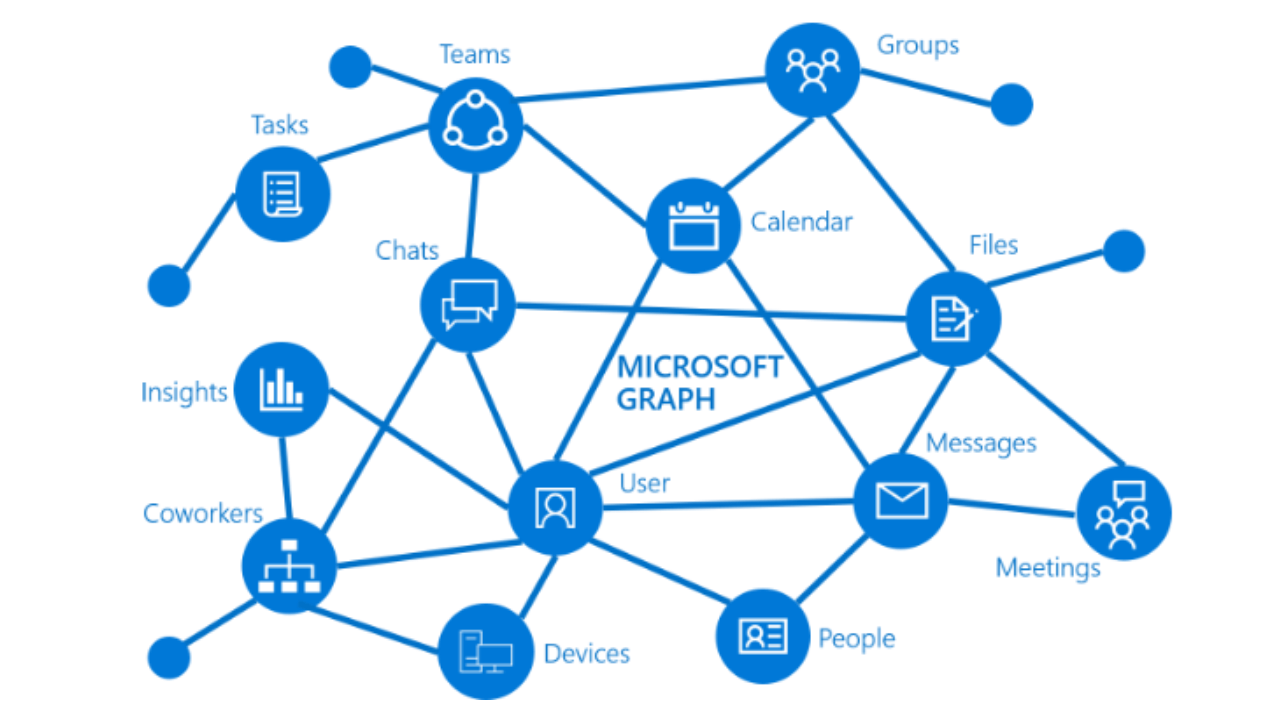
Disable Azure AD user account using Microsoft Graph and an application client
This post shows how to enable, disable or remove Azure AD user accounts using Microsoft Graph and a client credentials client. The Microsoft Graph client uses an application scope and application client. This is also possible using a delegated client. If using an application which has no user, an application scope is used to authorize […]
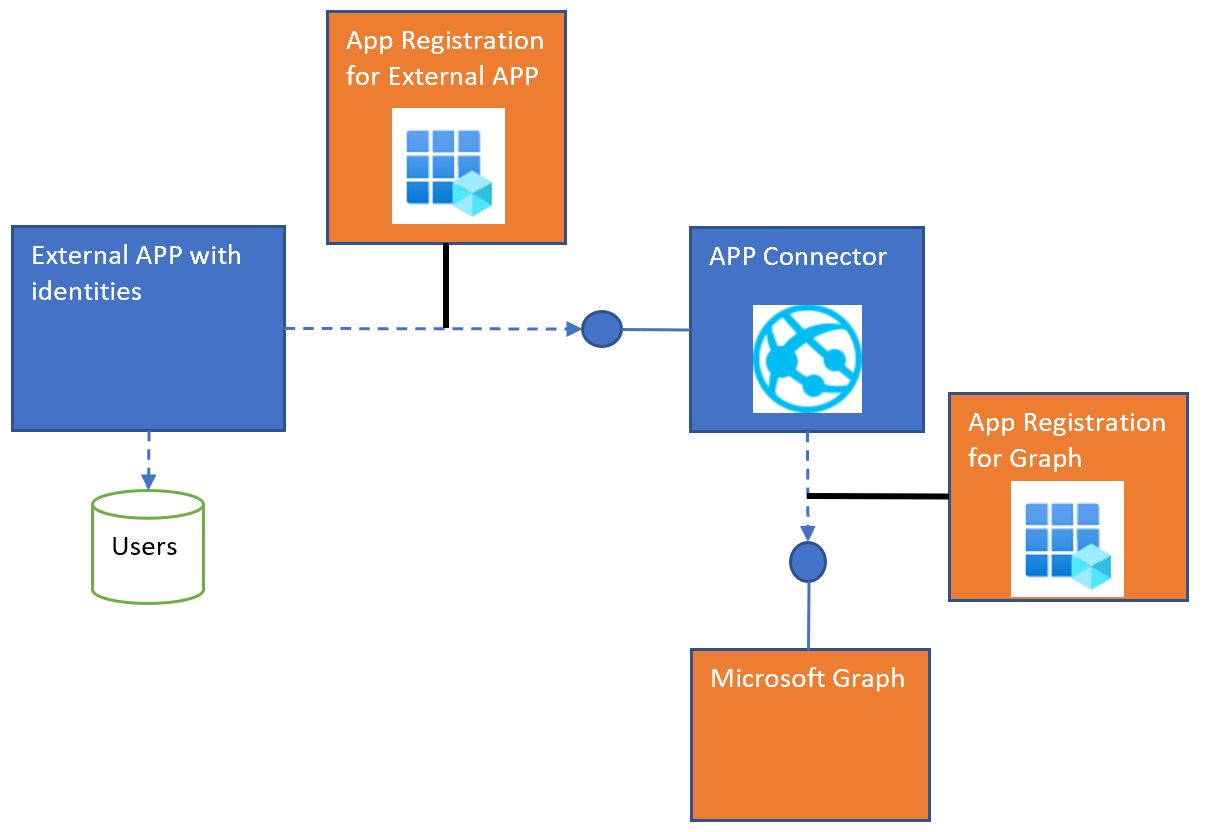
Invite external users to Azure AD using Microsoft Graph and ASP.NET Core
This post shows how to invite new Azure AD external guest users and assign the users to Azure AD groups using an ASP.NET Core APP Connector to import or update existing users from an external IAM and synchronize the users in Azure AD. The authorization can be implemented using Azure AD groups and can be […]
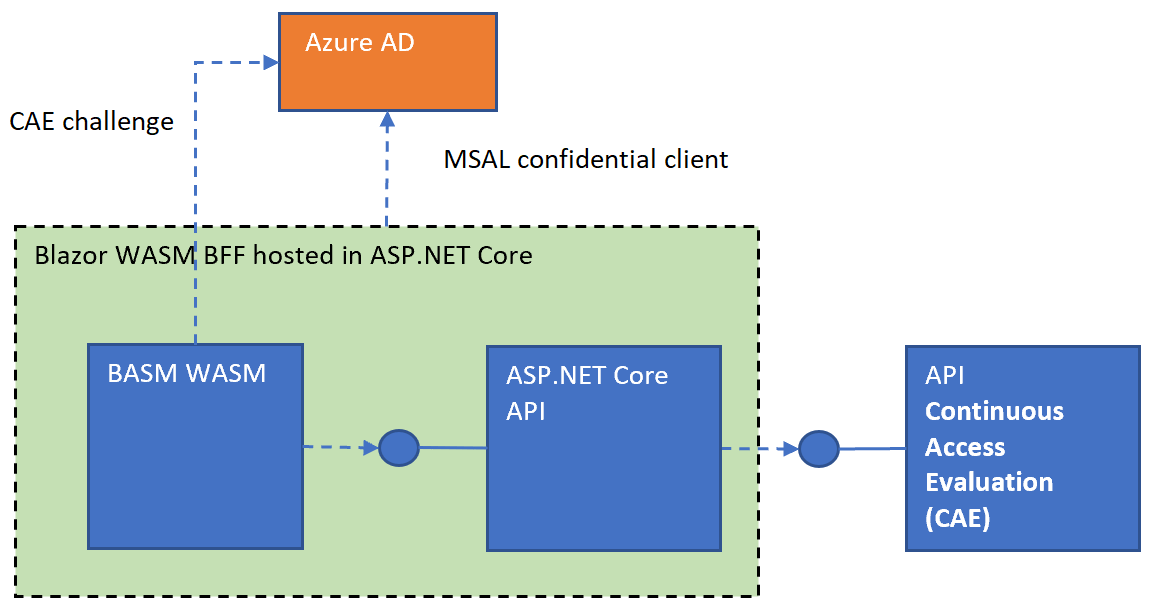
Force MFA in Blazor using Azure AD and Continuous Access
This article shows how to force MFA from your application using Azure AD and a continuous access auth context. When producing software which can be deployed to multiple tenants, instead of hoping IT admins configure this correctly in their tenants, you can now force this from the application. Many tenants do not force MFA. Code: […]
Implement Azure AD Continuous Access (CA) step up with ASP.NET Core Blazor using a Web API
This article shows how to implement Azure AD Continuous Access (CA) in a Blazor application which uses a Web API. The API requires an Azure AD conditional access authentication context. In the example code, MFA is required to use the external API. If a user requests data from the API using the required access token […]
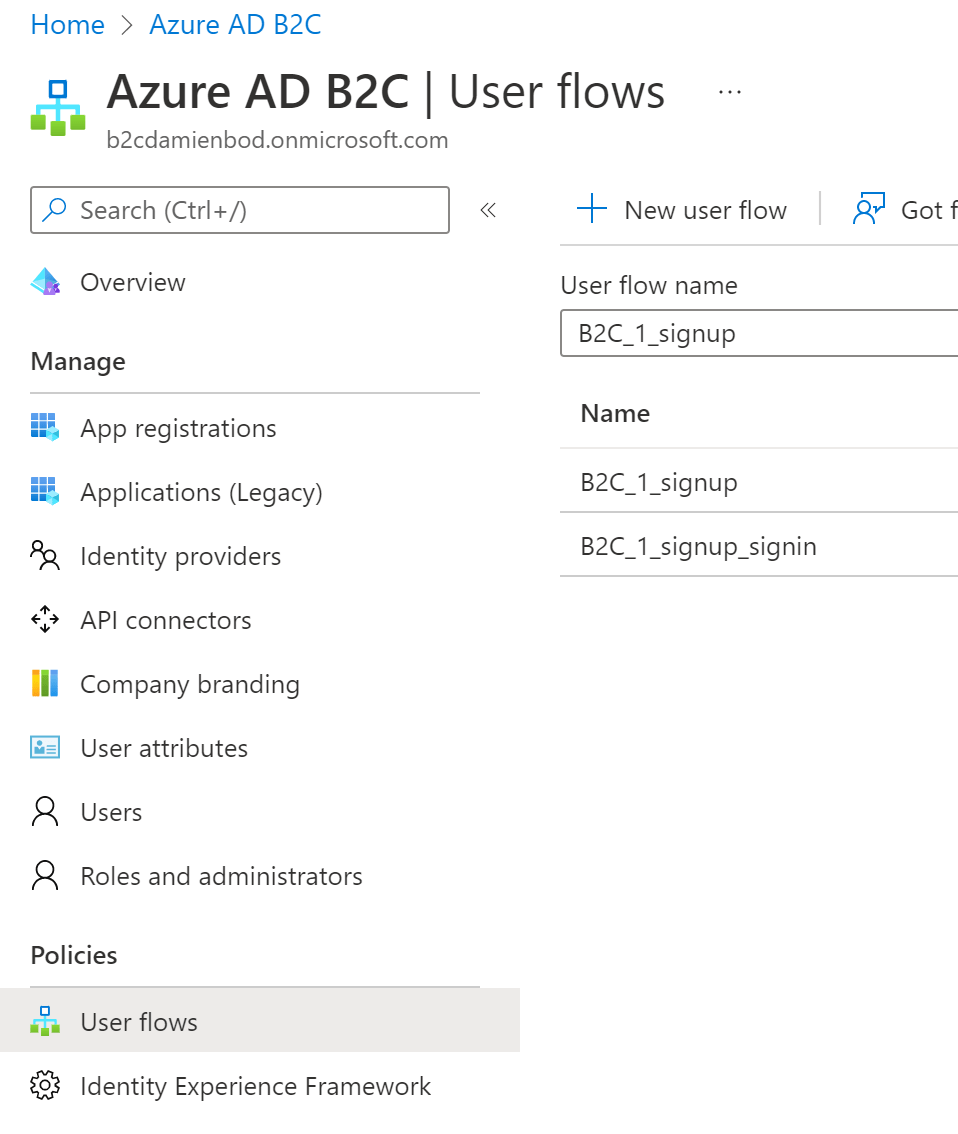
Using multiple Azure B2C user flows from ASP.NET Core
This article shows how to use multiple Azure B2C user flows from a single ASP.NET Core application. Microsoft.Identity.Web is used to implement the authentication in the client. This is not so easy to implement with multiple schemes as the user flow policy is used in most client URLs and the Microsoft.Identity.Web package overrides an lot […]
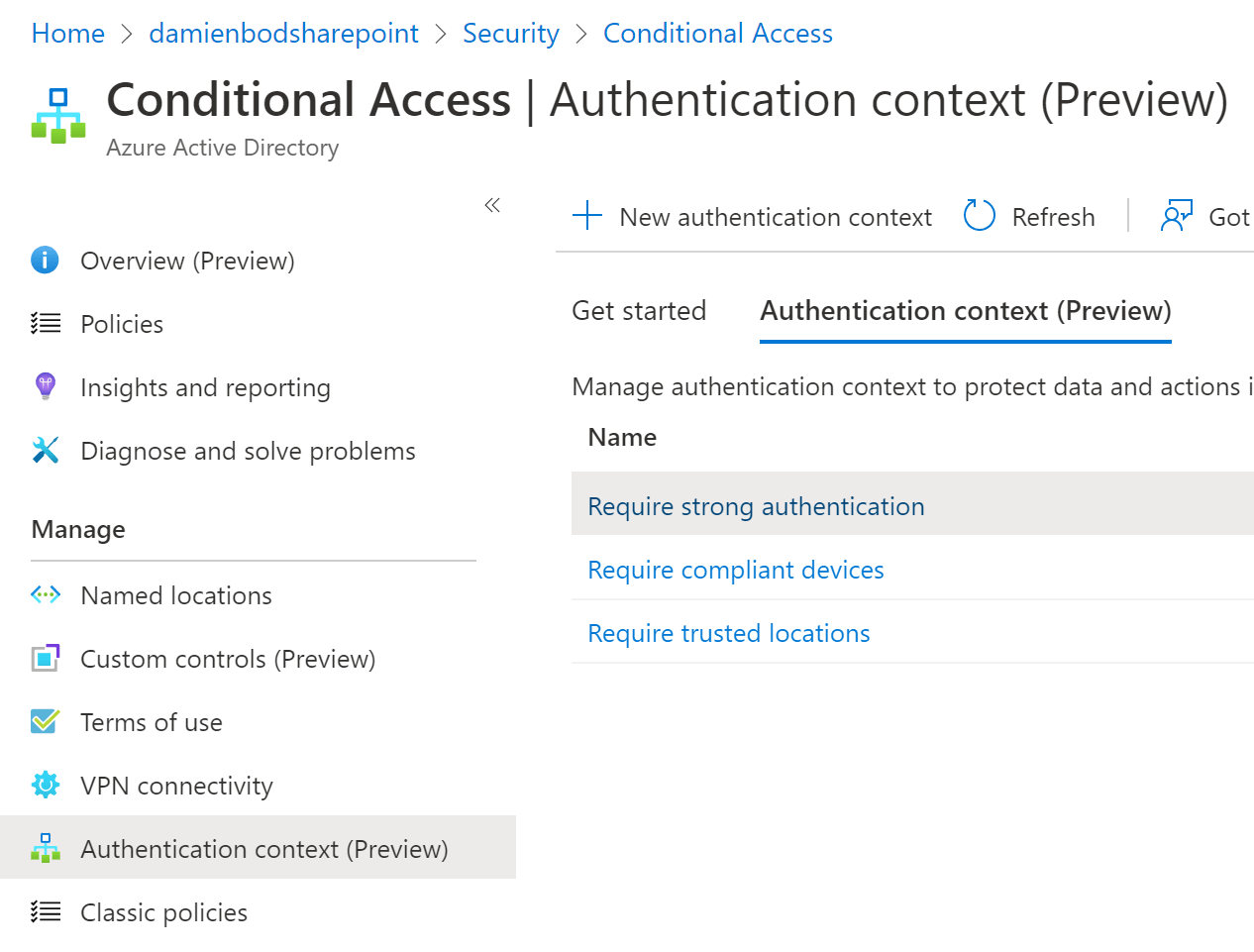
Implement Azure AD Continuous Access in an ASP.NET Core Razor Page app using a Web API
This article shows how Azure AD continuous access (CA) can be used in an ASP.NET Core UI application to force MFA when using an administrator API from a separate ASP.NET Core application. Both applications are secured using Microsoft.Identity.Web. An ASP.NET Core Razor Page application is used to implement the UI application. The API is implemented […]
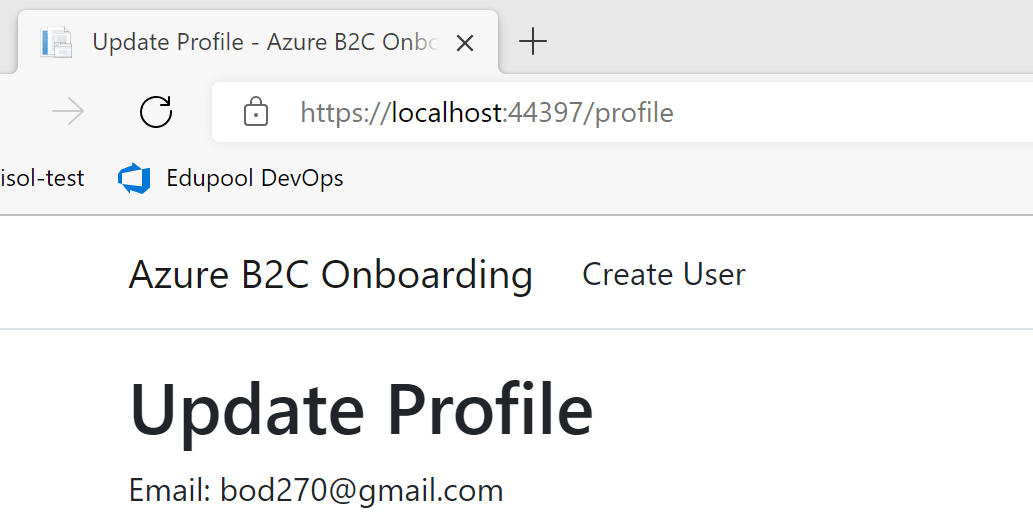
Onboarding new users in an ASP.NET Core application using Azure B2C
This article shows how to onboard new users into your ASP.NET Core application using Azure B2C as the identity provider and the account management. The software has application specific persisted user data and this user data needs to be connected to the identity data from the corresponding user in Azure B2C. Code: https://github.com/damienbod/azureb2c-fed-microsoft-entra-id History 2024-01-02 […]

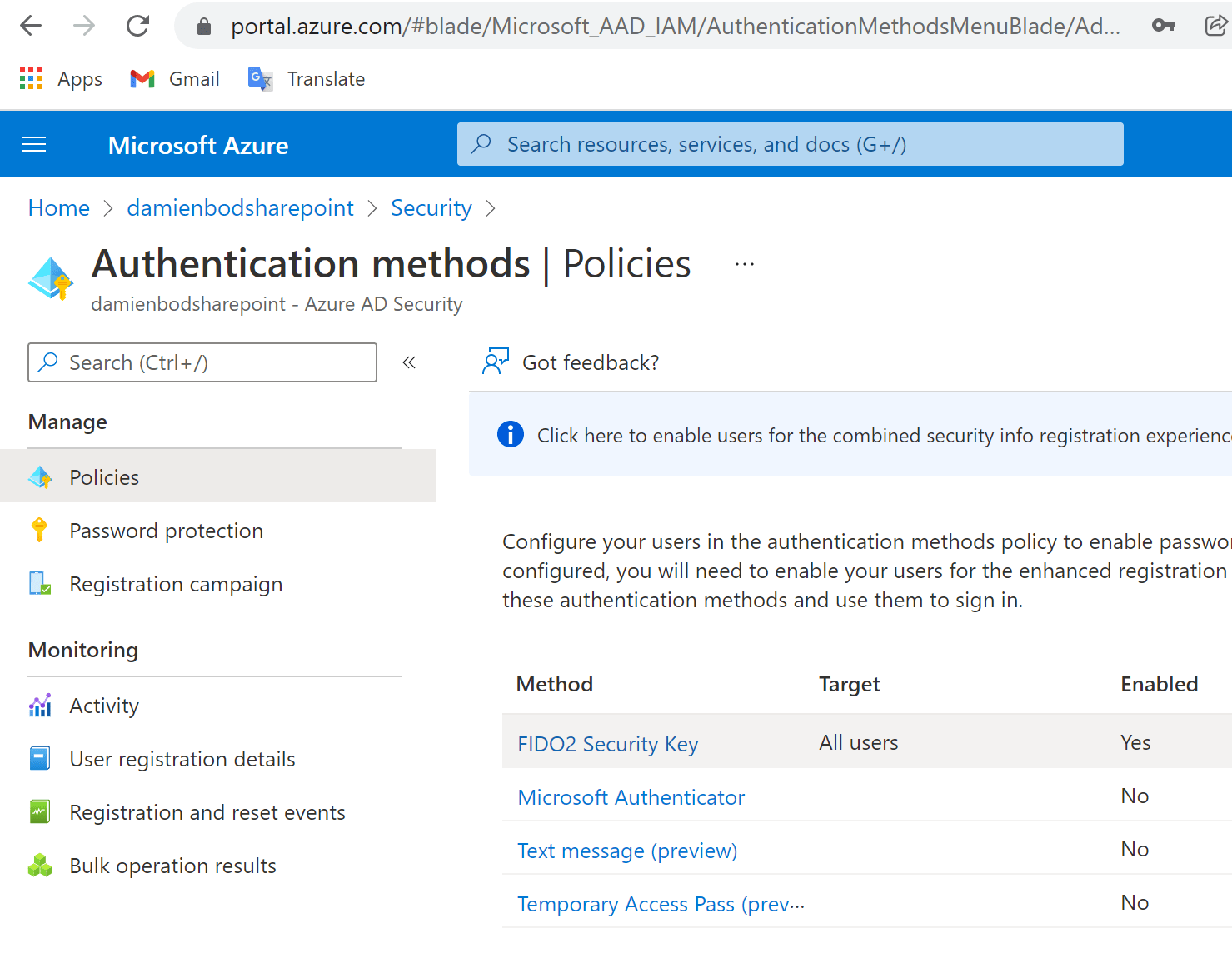
Use FIDO2 passwordless authentication with Azure AD
This article shows how to implement FIDO2 passwordless authentication with Azure AD for users in an Azure tenant. FIDO2 provides one of the best user authentication methods and is a more secure authentication compared with other account authentication implementations such authenticator apps, SMS, email, password alone or SSI authentication. FIDO2 authentication protects against phishing. To […]
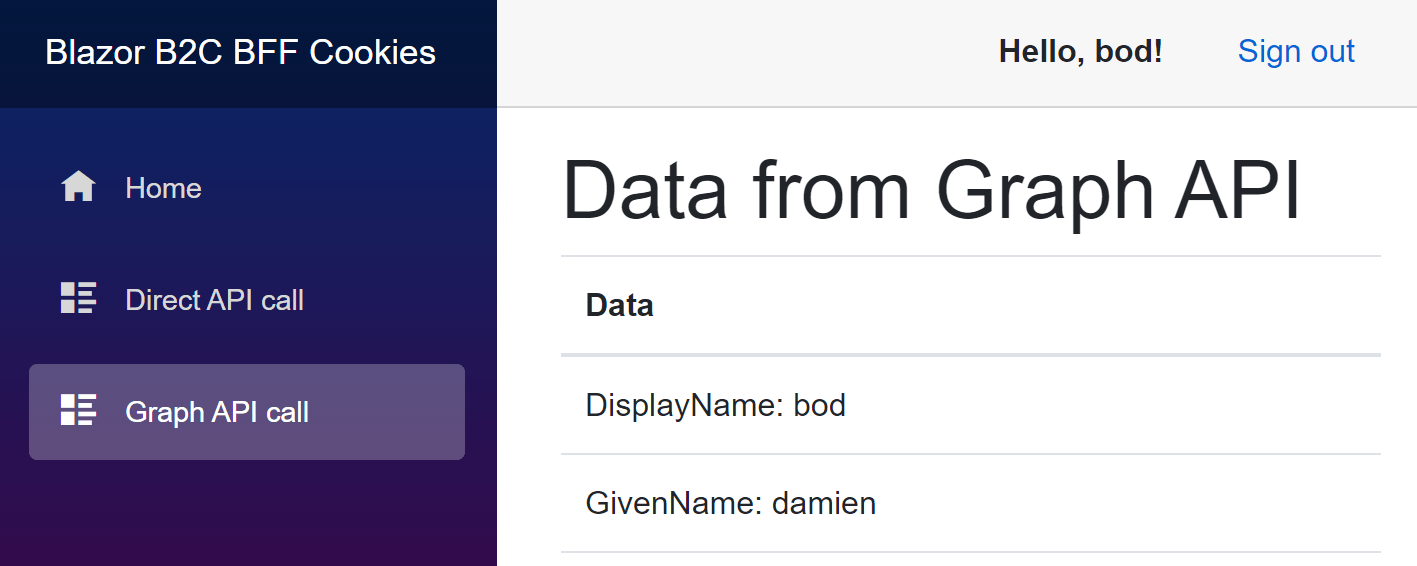
Blazor WASM hosted in ASP.NET Core templates with Azure B2C and Azure AD authentication using Backend for Frontend (BFF)
I have implemented many Blazor WASM ASP.NET Core hosted applications now for both Azure AD and Azure B2C authentication. I always implement security for this type of application now using the Backend for Frontend (BFF) security architecture and can remove the tokens from the client. This is also what I recommend. At present, no Microsoft […]
