Category Security

Add a Swagger UI using a .NET 9 Json OpenAPI file
This post shows how to implement a Swagger UI using a .NET 9 produced OpenAPI file. The Swagger UI is deployed to a secure or development environment and is not deployed to a public production target. Sometimes, it is required to deploy the Swagger UI to a development deployment target and not the test or […]
Sonar Webinar, end to end security of a web application
I did a Webinar on application security with Denis Troller and Sonar. I would like to thank Sonar for this opportunity, I really enjoyed it and found doing this together with you really professional, pleasant and fun to do. Here’s the recording: Link to the Sonar Q&A: https://community.sonarsource.com/t/webinar-end-to-end-security-in-a-web-application/115405 Link to the repository: https://github.com/damienbod/EndToEndSecurity

BFF secured ASP.NET Core application using downstream API and an OAuth client credentials JWT
This article shows how to implement a web application using backend for frontend security architecture for authentication and consumes data from a downstream API protected using a JWT access token which can only be accessed using an app-to-app access token. The access token is acquired using the OAuth2 client credentials flow and the API does […]

Migrate ASP.NET Core Blazor Server to Blazor Web
This article shows how to migrate a Blazor server application to a Blazor Web application. The migration used the ASP.NET Core migration documentation, but this was not complete and a few extra steps were required. The starting point was a Blazor Server application secured using OpenID Connect for authentication. The target system is a Blazor […]

Securing a Blazor Server application using OpenID Connect and security headers
This article shows how to secure a Blazor Server application. The application implements an OpenID Connect confidential client with PKCE using .NET 8 and configures the security headers as best possible for the Blazor Server application. OpenIddict is used to implement the identity provider and the OpenID Connect server. Code: https://github.com/damienbod/BlazorServerOidc OpenID Connect flow In […]
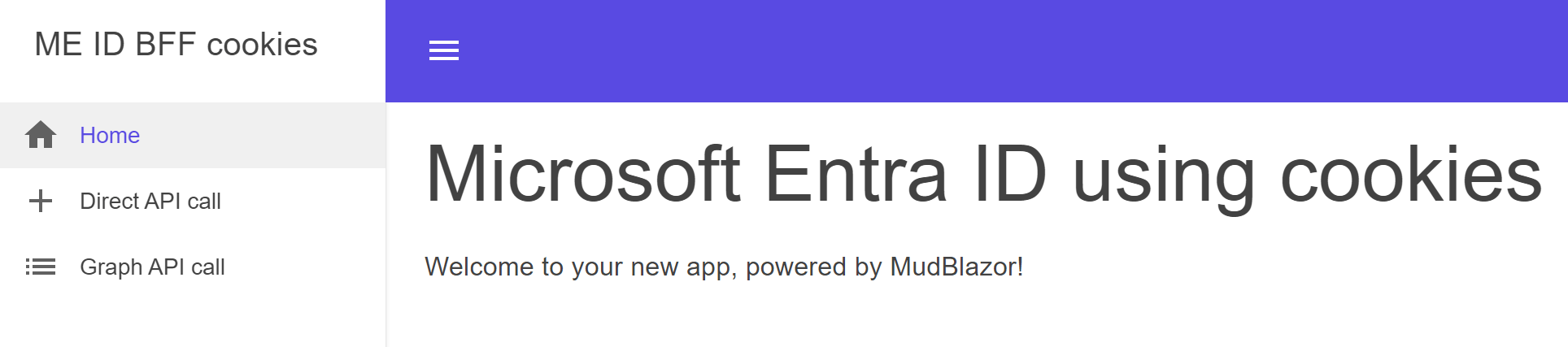
Securing a MudBlazor UI web application using security headers and Microsoft Entra ID
This article shows how a Blazor application can be implemented in a secure way using MudBlazor UI components and Microsoft Entra ID as an identity provider. The MudBlazor UI components adds some inline styles and requires a specific CSP setup due to this and the Blazor WASM script requirements. Code: https://github.com/damienbod/MicrosoftEntraIDMudBlazor Setup The application is […]

Authentication with multiple identity providers in ASP.NET Core
This article shows how to implement authentication in ASP.NET Core using multiple identity providers or secure token servers. When using multiple identity providers, the authentication flows need to be separated per scheme for the sign-in flow and the sign-out flow. The claims are different and would require mapping logic depending on the authorization logic of […]

Fix missing tokens when using downstream APIs and Microsoft Identity in ASP.NET Core
This article shows how a secure ASP.NET Core application can use Microsoft Entra ID downstream APIs and an in-memory cache. When using in-memory cache and after restarting an application, the tokens are missing for a value session stored in the cookie. The application needs to recover. Code: https://github.com/damienbod/bff-aspnetcore-angular OpenID Connect client setup The ASP.NET Core […]
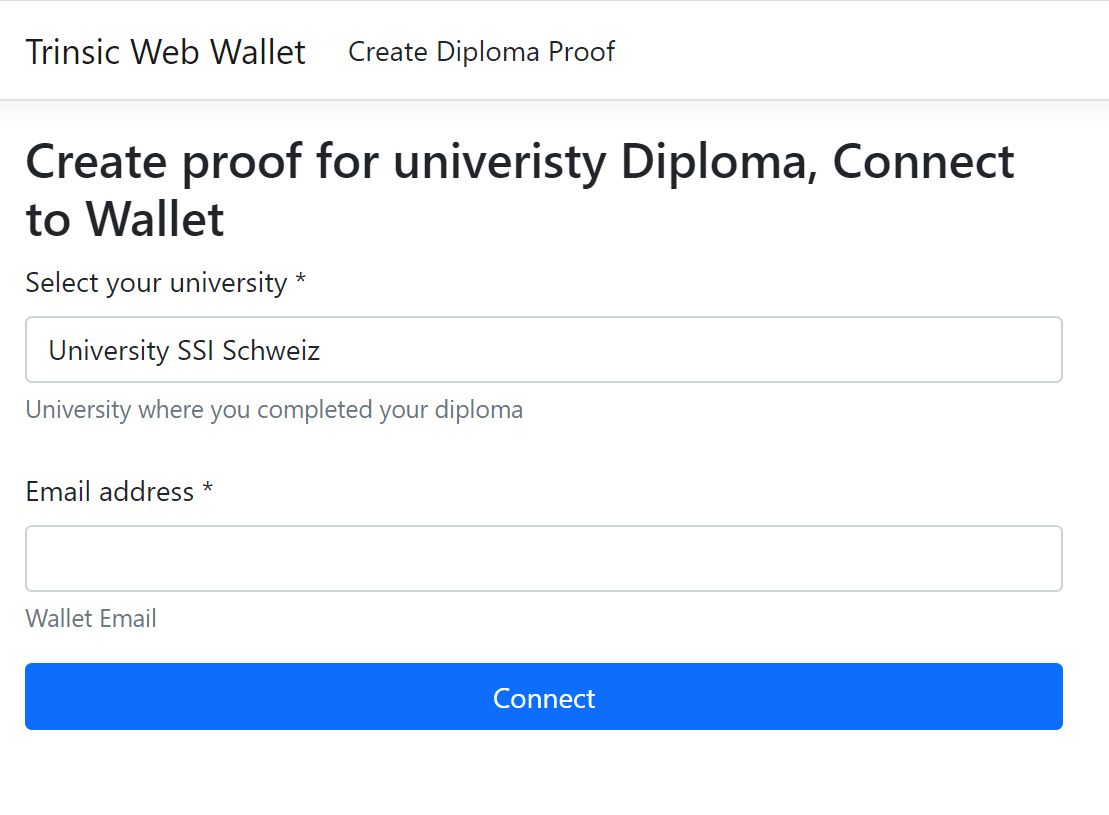
Issue and verify BBS+ verifiable credentials using ASP.NET Core and trinsic.id
This article shows how to implement identity verification in a solution using ASP.NET Core and trinsic.id, built using an id-tech solution based on self sovereign identity principals. The credential issuer uses OpenID Connect to authenticate, implemented using Microsoft Entra ID. The edge or web wallet authenticates using trinsic.id based on a single factor email code. […]

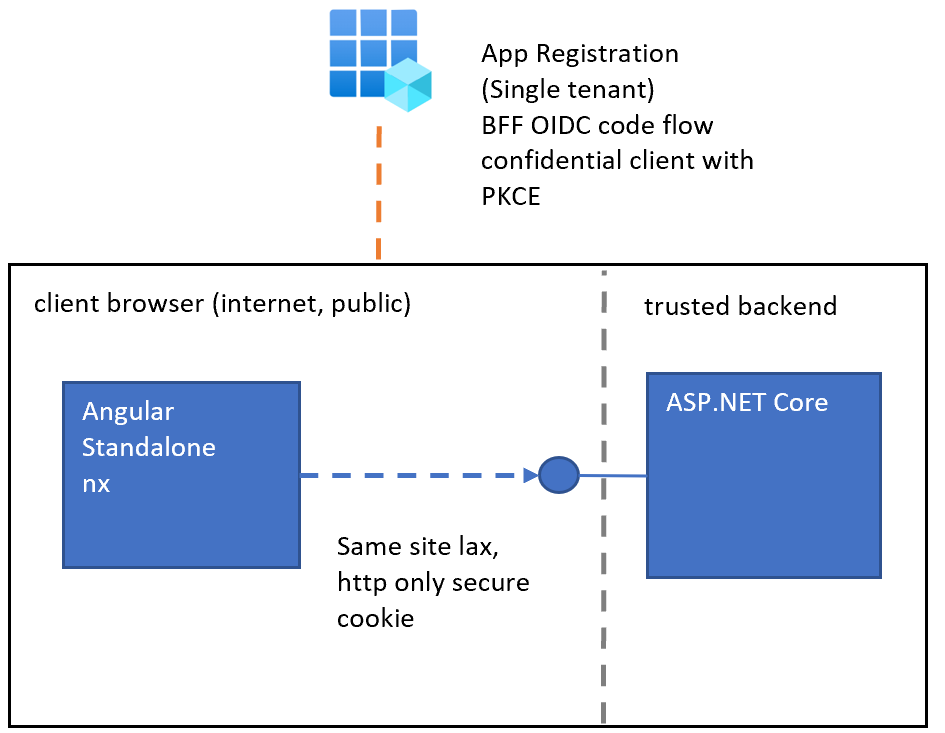
Secure Angular application using OpenIddict and ASP.NET Core with BFF
The article shows how an Angular nx Standalone UI hosted in an ASP.NET Core application can be secured using cookies. OpenIddict is used as the identity provider. The trusted application is protected using the Open ID Connect code flow with a secret and using PKCE. The API calls are protected using the secure cookie and anti-forgery […]
