Category OAuth2
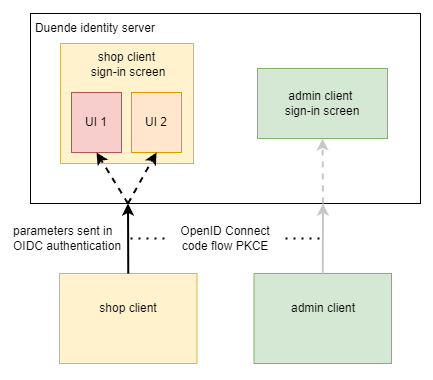
Customizing a single client sign-in using parameters in Duende IdentityServer
This post looks at customizing the sign-in UI and the sign-in options in an ASP.NET Core application using Duende IdentityServer and ASP.NET Core Identity. There are multiple ways of changing the look and feel of the UI for different OpenID Connect clients or different client flows. In the previous post, the UI was customized per […]

ASP.NET Core delegated OAuth Token Exchange access token management
This blog shows how to implement a delegated OAuth 2.0 Token Exchange RFC 8693 flow in ASP.NET Core, and has a focus on access token management. It looks at how the OAuth Token Exchange can be implemented and how an application can request delegated access tokens on behalf of a user and another application, providing […]

ASP.NET Core user application access token management
This article looks at management application access tokens in an ASP.NET Core web application. Any application with or without a user can use application access tokens as long as the application can persist the tokens in a safe way. Code: https://github.com/damienbod/token-mgmt-ui-application Blogs in this series Setup The ASP.NET Core web application authenticates using OpenID Connect […]

Using Entra External ID with an Auth0 OpenID Connect identity provider
This post looks at implementing an Open ID Connect identity provider in Microsoft Entra External ID. Auth0 is used as the identity provider and an ASP.NET Core application is used to test the authentication. Microsoft Entra External ID federates to Auth0. Client code: https://github.com/damienbod/EntraExternalIdCiam Microsoft Entra External ID supports federation using OpenID Connect and was […]

ASP.NET Core and Angular BFF using a YARP downstream API protected using certificate authentication
This article demonstrates how to implement a downstream API protected by certificate authentication using Microsoft YARP reverse proxy in an ASP.NET Core web application. The application uses Angular for its UI and secures both the UI and the ASP.NET Core backend through a backend-for-frontend security architecture. The downstream API is secured with certificate authentication and […]

Implement OpenID Connect Back-Channel Logout using ASP.NET Core, Keycloak and .NET Aspire
This post shows how to implement an OpenID Connect back-channel logout using Keycloak, ASP.NET Core and .NET Aspire. The Keycloak and the Redis cache are run as containers using .NET Aspire. Two ASP.NET Core UI applications are used to demonstrate the server logout. Code: https://github.com/damienbod/keycloak-backchannel Setup The applications are run and tested using .NET Aspire. […]

Implement ASP.NET Core OpenID Connect OAuth PAR client with Keycloak using .NET Aspire
This post shows how to implement an ASP.NET Core application which uses OpenID Connect and OAuth PAR for authentication. The client application uses Keycloak as the identity provider. The Keycloak application is hosted in a docker container. The applications are run locally using .NET Aspire. This makes it really easy to develop using containers. Code: […]

Add a Swagger UI using a .NET 9 Json OpenAPI file
This post shows how to implement a Swagger UI using a .NET 9 produced OpenAPI file. The Swagger UI is deployed to a secure or development environment and is not deployed to a public production target. Sometimes, it is required to deploy the Swagger UI to a development deployment target and not the test or […]
Sonar Webinar, end to end security of a web application
I did a Webinar on application security with Denis Troller and Sonar. I would like to thank Sonar for this opportunity, I really enjoyed it and found doing this together with you really professional, pleasant and fun to do. Here’s the recording: Link to the Sonar Q&A: https://community.sonarsource.com/t/webinar-end-to-end-security-in-a-web-application/115405 Link to the repository: https://github.com/damienbod/EndToEndSecurity

BFF secured ASP.NET Core application using downstream API and an OAuth client credentials JWT
This article shows how to implement a web application using backend for frontend security architecture for authentication and consumes data from a downstream API protected using a JWT access token which can only be accessed using an app-to-app access token. The access token is acquired using the OAuth2 client credentials flow and the API does […]
