Category .NET Core

Use client assertions in OpenID Connect and ASP.NET Core
Client assertions is a method of client authentication which can be used in OpenID Connect. This provides an alternative to client secrets. This approach enhances security by using signed tokens (JWTs) to authenticate clients during the token request process or the OAuth PAR request. In ASP.NET Core, client assertions is not supported per default, a […]
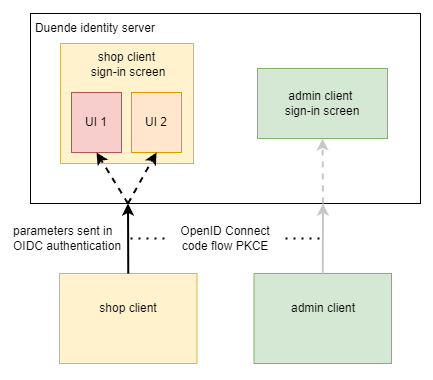
Customizing a single client sign-in using parameters in Duende IdentityServer
This post looks at customizing the sign-in UI and the sign-in options in an ASP.NET Core application using Duende IdentityServer and ASP.NET Core Identity. There are multiple ways of changing the look and feel of the UI for different OpenID Connect clients or different client flows. In the previous post, the UI was customized per […]

ASP.NET Core delegated OAuth Token Exchange access token management
This blog shows how to implement a delegated OAuth 2.0 Token Exchange RFC 8693 flow in ASP.NET Core, and has a focus on access token management. It looks at how the OAuth Token Exchange can be implemented and how an application can request delegated access tokens on behalf of a user and another application, providing […]

ASP.NET Core user application access token management
This article looks at management application access tokens in an ASP.NET Core web application. Any application with or without a user can use application access tokens as long as the application can persist the tokens in a safe way. Code: https://github.com/damienbod/token-mgmt-ui-application Blogs in this series Setup The ASP.NET Core web application authenticates using OpenID Connect […]

ASP.NET Core user delegated access token management
The article looks at managing user delegated access tokens for a downstream API in an ASP.NET Core web application. There are many ways of implementing this, all with advantages and disadvantages. The tokens are requested from an OpenID Connect server using the recommended standards. In this blog, the UI access token from the application authentication […]

Implement security headers for an ASP.NET Core API supporting OpenAPI Swagger UI
This article shows how to implement security headers for an application supporting an API and a swagger UI created from a open API in .NET 9. The security headers are implemented using the NetEscapades.AspNetCore.SecurityHeaders Nuget packages from Andrew Lock. Code: https://github.com/damienbod/WebApiOpenApi Deploying a web application which supports both an API and a UI have different […]
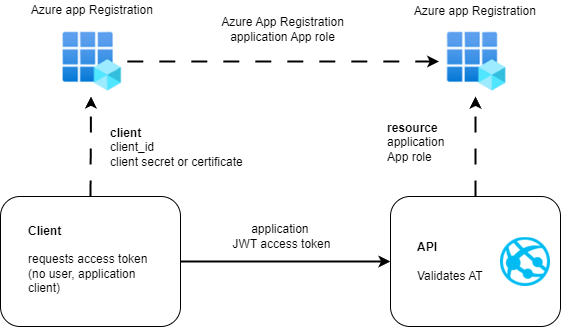
Microsoft Entra ID App-to-App security architecture
This article looks at the different setups when using App-to-App security with Microsoft Entra ID (OAuth client credentials). Microsoft Entra App registrations are used to configure the OAuth clients and resources. For each tenant, an Enterprise application is created for the client App registration when the consent is granted. The claims in the access token […]

Implement a Geo-distance search using .NET Aspire, Elasticsearch and ASP.NET Core
This article shows how to implement a geo location search in an ASP.NET Core application using a LeafletJs map. The selected location can be used to find the nearest location with an Elasticsearch Geo-distance query. The Elasticsearch container and the ASP.NET Core UI application are setup for development using .NET Aspire. Code: https://github.com/damienbod/WebGeoElasticsearch Setup For […]

Using Elasticsearch with .NET Aspire
This post shows how to use Elasticsearch in .NET Aspire. Elasticsearch is setup to use HTTPS with the dotnet developer certificates and and simple client can be implemented to query the data. Code: https://github.com/damienbod/keycloak-backchannel Setup Two services are setup to run in .NET Aspire. The first service is the official Elasticsearch docker container and deployed […]

Implement ASP.NET Core OpenID Connect OAuth PAR client with Keycloak using .NET Aspire
This post shows how to implement an ASP.NET Core application which uses OpenID Connect and OAuth PAR for authentication. The client application uses Keycloak as the identity provider. The Keycloak application is hosted in a docker container. The applications are run locally using .NET Aspire. This makes it really easy to develop using containers. Code: […]
