Category Azure Key Vault
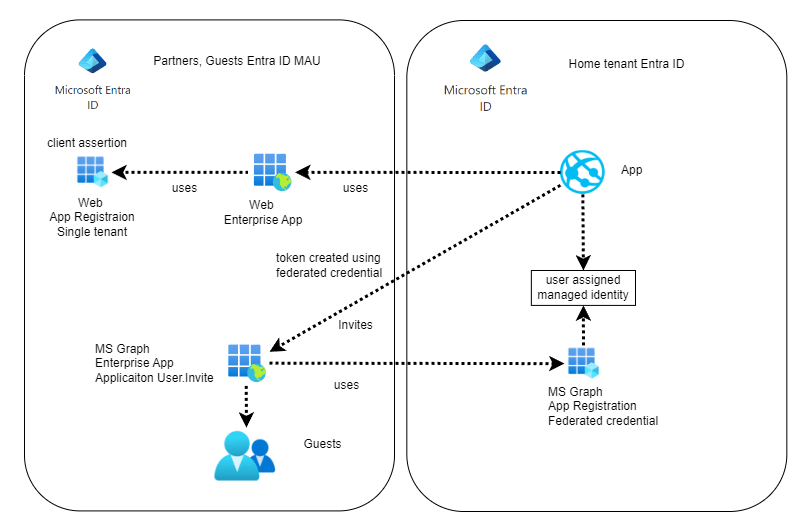
Invite Guest users in a Entra ID Multi-tenant setup
This post looks at implementing a guest user invite in a cross tenant setup. This is useful when creating partner tenants using an Entra ID MAU license for all partner guests and members. This makes it possible to keep the home tenant separated for internal members. Setup The Partners or guest Entra ID tenant is […]
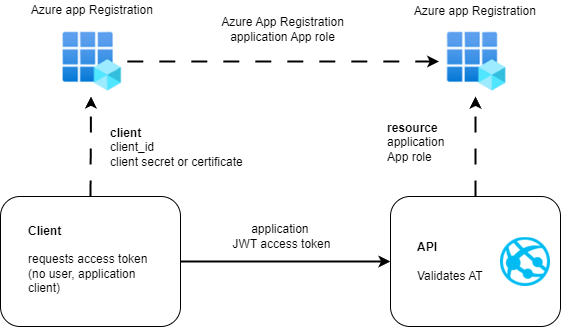
Microsoft Entra ID App-to-App security architecture
This article looks at the different setups when using App-to-App security with Microsoft Entra ID (OAuth client credentials). Microsoft Entra App registrations are used to configure the OAuth clients and resources. For each tenant, an Enterprise application is created for the client App registration when the consent is granted. The claims in the access token […]

Debug Logging Microsoft.Identity.Client and the MSAL OAuth client credentials flow
This post shows how to add debug logging to the Microsoft.Identity.Client MSAL client which is used to implement an OAuth2 client credentials flow using a client assertion. The client uses the MSAL nuget package. PII logging was activated and the HttpClient was replaced to log all HTTP requests and responses from the MSAL package. Code: […]
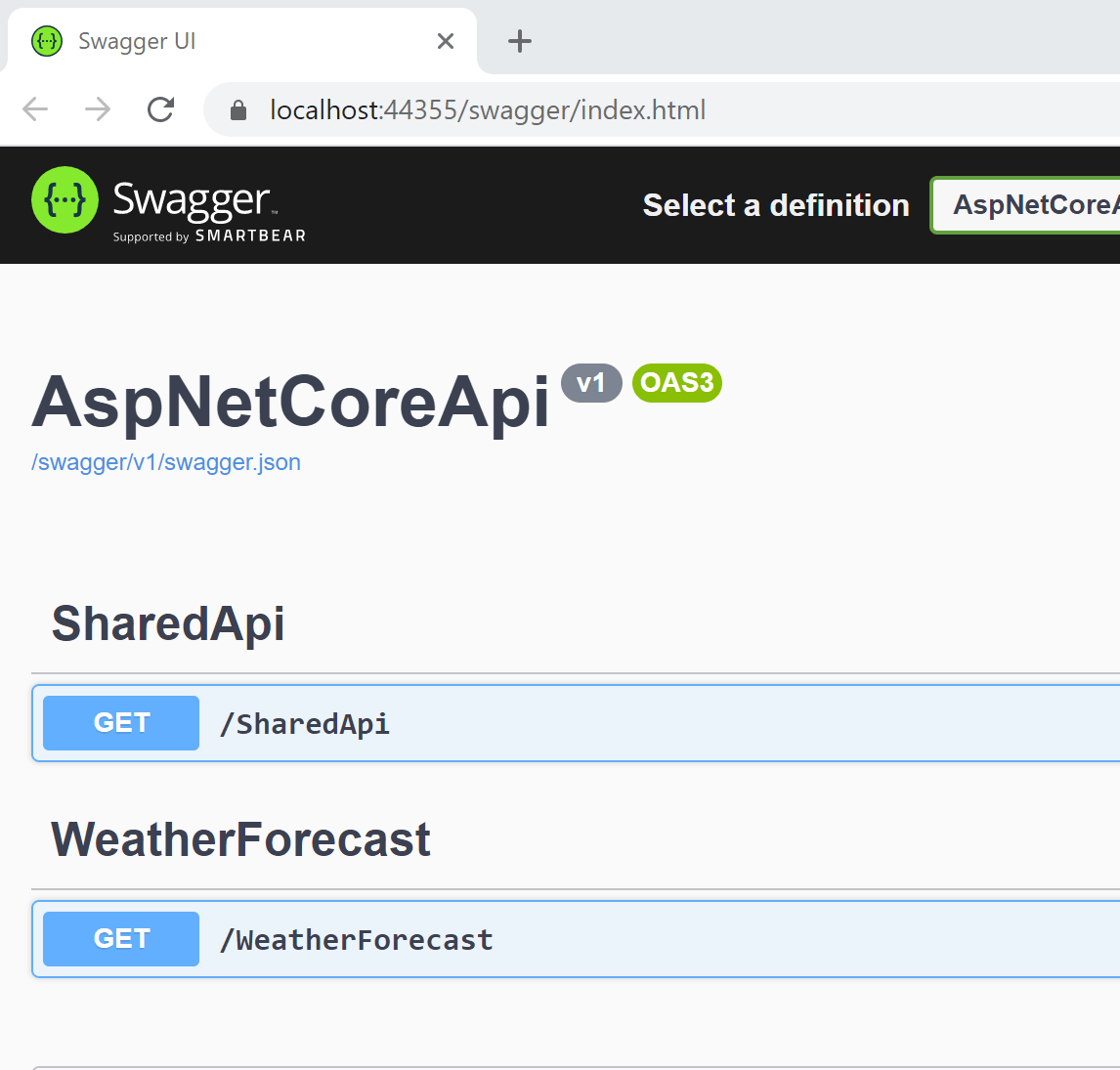
Using encrypted access tokens in Azure with Microsoft.Identity.Web and Azure App registrations
This post shows how to use encrypted access tokens with Microsoft Entra ID App registrations using Microsoft.Identity.Web. By using encrypted access tokens, only applications with access to the private key can decrypt the tokens. When using encrypted tokens, you can prevent access tokens data being used or read by such tools as https://jwt.ms or https://jwt.io […]

Using Key Vault certificates with Microsoft.Identity.Web and ASP.NET Core applications
This post shows how Azure Key Vault certificates can be used with Microsoft.Identity.Web in an ASP.NET Core application which requires a downstream “access_as_user” API. The Microsoft Entra ID App Registrations requires a certificate instead of a client secret. Code: https://github.com/damienbod/MicrosoftEntraIDAuthMicrosoftIdentityWeb Posts in this series History 2023-11-28 Updated to .NET 8 Creating the Key Vault certificates […]

Implement Microsoft Entra ID Client credentials flow using Client Certificates for service APIs
This post shows how to implement an Microsoft Entra ID client credential flows to access an API for a service-to-service connection. No user is involved in this flow. A client certificate (Private Key JWT authentication) is used to get the access token and the token is used to access the API which is then used […]
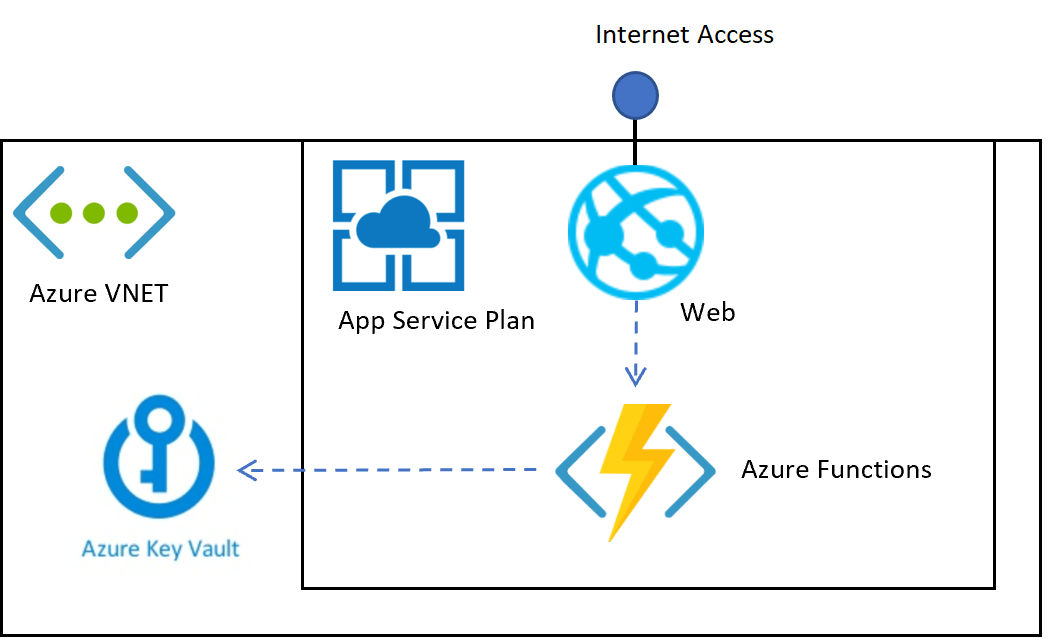
Securing Azure Key Vault inside a VNET and using from an Azure Function
This post shows how an Azure Key Vault can be protected inside an Azure virtual network. The deployment is setup so that only applications in the same VNET can access the Key Vault. To implement this, the access to the Key Vault is restricted to the VNET and secondly, the applications accessing the Key Vault […]

Securing Azure Functions using an Azure Virtual Network
In this post, an Azure Function is deployed in a Azure Virtual Network and the access to the Azure Function is restricted so that it cannot be reach from the Internet. Only Applications deployed in the same VNET can access the Azure Functions. Code: https://github.com/damienbod/AzureFunctionsSecurity History Blogs in the series Target Setup The Virtual network […]
Using Key Vault and Managed Identities with Azure Functions
This article shows how Azure Key Vault could be used together with Azure Functions. The Azure Functions can use the system assigned identity to access the Key Vault. This needs to be configured in the Key Vault access policies using the service principal. By using the Microsoft.Azure.KeyVault and the Microsoft.Extensions.Configuration.AzureKeyVault nuget packages, defining direct references […]

Azure Functions Configuration and Secrets Management
This post shows how to configure Azure Function projects so that no secrets are required in the local.settings.json or in the code. Secrets for the project are saved in the user secrets of the project, or in the app settings of the deployment. The deployment should/can use Azure Key Vault for the secrets and not […]
